When a company is preparing to acquire, or be acquired, technology is often treated as a line item in a spreadsheet. But the truth is, the state of a business’s technology stack can make or break the success of a transaction. That’s why Stelth treats technical due diligence as both a discovery process and a foundation for integration.
We don’t just review systems – we uncover patterns, risks, and untapped potential across infrastructure, platforms, processes, and people. Our process is quiet, thorough, and designed to give decision-makers exactly what they need: clarity.
Why IT Due Diligence Matters
Most M&A failure points aren’t about strategy, they’re about execution. Execution starts with knowing what you’re walking into. When technology due diligence is skipped or surface-level, the result is often:
-
Hidden technical debt that delays integration
-
Overlapping platforms and inflated licensing costs
-
Security or compliance gaps that emerge post-close
-
Underestimated complexity that derails operational planning
Done right, due diligence doesn’t just reveal risks – it creates an integration playbook.
Our Due Diligence Process
At Stelth, we break technical due diligence into five key areas:
1. Infrastructure & Systems Landscape
We catalog every major system that powers the business: ERP, CRM, OMS, EHRs, file servers, backup systems, domain controllers, cloud platforms, and more.
But we don’t just list what exists- we ask the deeper questions:
-
Are systems cloud-hosted or on-prem?
-
Are there brittle custom integrations?
-
Is shadow IT operating beneath the surface?
-
Are data flows clean, or duplicated across departments?
We produce diagrams that map the entire environment – from apps and networks to DNS zones and Active Directory forests.
2. Security & Compliance Posture
Before a transaction, we help you answer: Is this environment secure enough to inherit?
We review:
-
MFA enforcement and access controls
-
Role-based permissions across cloud and on-prem tools
-
Patch management processes
-
Antivirus, endpoint protection, and firewall configurations
-
Logging and alerting maturity
We also assess alignment to frameworks like SOC 2 and HITRUST – depending on industry and risk profile.
3. Vendor & Licensing Review
Most companies accumulate vendors and tools without regular rationalization. We analyze:
-
Vendor contracts and renewals
-
Overlapping platforms (e.g., two CRMs or multiple backup tools)
-
Licensing models (per user, device, org)
-
Support responsiveness and exit clauses
Our goal: streamline vendor sprawl and highlight which relationships to keep, consolidate, or sunset post-close.
4. Internal Team & Operational Maturity
Technology doesn’t run itself. We evaluate the internal IT structure by reviewing:
-
Organizational charts and reporting lines
-
Skill sets, certifications, and responsibilities
-
Third-party reliance (fully outsourced vs. hybrid)
-
Change management and documentation practices
-
Ticketing systems and service workflows
This helps anticipate which team members will be critical post-close, and where additional support may be needed.
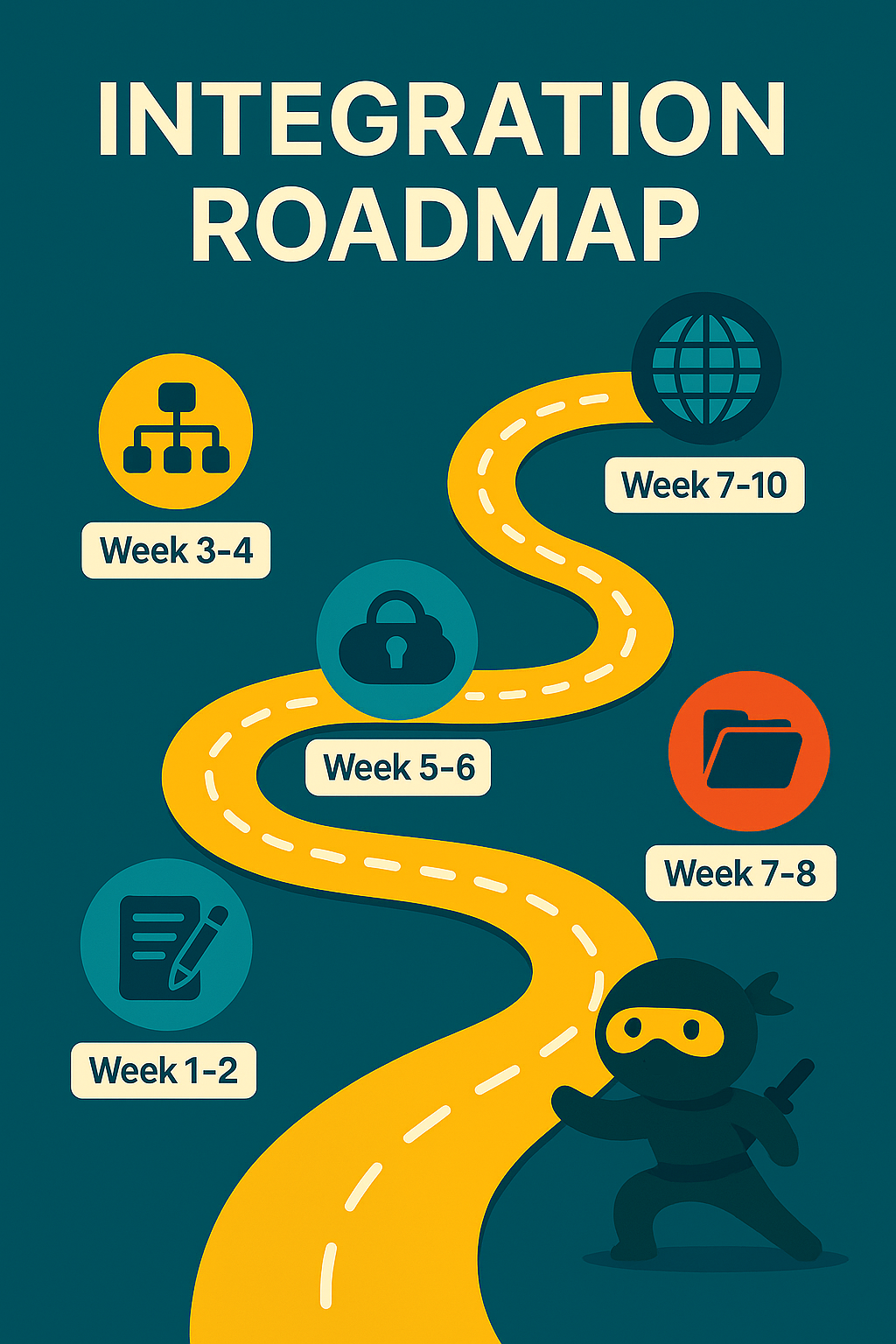
5. Integration Readiness
We use the diligence phase to begin modeling how systems could (or should) come together. That includes:
-
Email domain strategy and coexistence
-
Active Directory trust or migration planning
-
File share overlaps and structure standardization
-
Consolidation of collaboration tools (Teams, SharePoint, etc.)
-
VPN redesign and network segmentation planning
By the time the deal closes, we’re not starting from scratch – we’re moving forward with purpose.
Deliverables You Can Use on Day One
We don’t bury you in documents. Our output is clean, visual, and designed for business decision-makers and technical implementers alike. This includes:
-
An executive-level risk and readiness summary
-
System and infrastructure maps
-
A prioritized integration opportunity matrix
-
Vendor analysis with cost and redundancy highlights
-
Actionable Day One IT recommendations
What Sets Us Apart
-
Hands-On Access When Possible: We don’t just send questionnaires = we connect to systems, pull real data, and verify configurations.
-
Contextual Understanding: We align our findings to your deal goals. Whether you’re merging teams or planning to operate as standalone, our analysis adapts.
-
Quiet Confidence: We operate discreetly, often behind NDAs or within larger deal teams, and respect the need for confidentiality and minimal disruption.
A Real-World Example
In recent acquisitions we handled, our team uncovered:
-
A homegrown middleware tool holding together two core systems with no failover
-
Two different backup providers – both misconfigured
-
A security vendor whose contract was set to auto-renew days after close at triple the market rate
-
An internal IT lead who had built most of the infrastructure but wasn’t included in early integration discussions
Each of these discoveries led to action plans that saved money, avoided outages, and preserved key talent.
Final Thought: It’s Not Just Risk – It’s Opportunity
Yes, due diligence identifies what’s broken or fragile – but just as often, it reveals where you can scale. That might mean consolidating onto a stronger platform, rolling out a mature security program, or elevating a high-performing IT team into a leadership role across the combined entity.
At Stelth, we believe due diligence is where transformation begins.